NSF awards $5.46 million to UC Berkeley and USC to build testbed for cyber war games
BERKELEY – Cyber war games will soon begin, and the players will be researchers seeking to protect networks from computer attacks. A three-year, $5.46 million grant from the National Science Foundation will establish a large-scale cybersecurity testbed for the development of new defenses against computer worms and viruses.
Researchers at the University of California, Berkeley, will partner with the University of Southern California's Information Sciences Institute (USC-ISI) in the project. Called the Cyber Defense Technology Experimental Research network, or DETER, the project arose from the need for a testbed that models the complex, heterogeneous nature of the Internet.
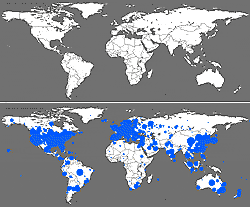 Cyberwarriors will be fighting a fast-spreading foe. These maps show the January 2003 spread of the Sapphire worm (also known as Slammer), growing from nothing (top) to global impact (blue zones at bottom) in only half an hour. (Courtesy CAIDA) |
"One of the challenges of creating effective defense programs for attacks from viruses and worms is that they are only tested in moderate-sized private research facilities or through computer simulations that are not representative of the way the Internet works in reality," said Shankar Sastry, UC Berkeley professor and chair of electrical engineering and computer sciences, and principal investigator of the project.
The NSF is collaborating with the U.S. Department of Homeland Security, which is helping fund the cybersecurity testbed.
"Through this project we will develop traffic models and architectures that are scaled down from the actual Internet, but still representative enough that people can have confidence in it," said Sastry, who in July 2003 testified before the Committee on Homeland Security in Congress regarding the need for such a testbed.
The ambitious project comes at a time when serious attacks on the Internet have become increasingly common. Researchers at the San Diego Supercomputer Center (SDSC) at UC San Diego recorded more than 12,000 denial-of-service attacks against 5,000 distinct targets, ranging from high profile e-commerce sites to small Internet service providers, during a three-week period in 2001. More recent studies by SDSC researchers found that in the past two years, the number of denial-of-service attacks has increased by a factor of 10.
Many destructive codes can cause significant disruption for businesses that rely upon a smoothly operating network. The Slammer/Sapphire worm, which broke speed records in January 2003 by infecting more than 75,000 hosts around the world within 10 minutes, led to ATM failures, network outages and disruptions in airline reservations.
In August alone, hundreds of thousands of computers that had not been updated with security patches became infected with MSBlaster and SoBig worms, crashing PCs, Web servers and transaction processing systems.
"With so much of the nation now dependent on the Internet, we are no longer talking about nuisance pranks and vandalism, but potential losses in the billions of dollars," said Terry Benzel, assistant director for special projects at USC-ISI and co-investigator of the project.
"These attacks in recent months clearly illustrate the need for better defense systems," said Ruzena Bajcsy, director of the UC Berkeley-based Center for Information Technology Research in the Interest of Society (CITRIS) and co-principal investigator of DETER. "One of the most important interests in CITRIS is to make the Internet free of worms and denial-of-service attacks."
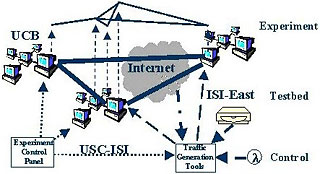 Arena architecture provides a mini-Internet for cyber crime fighters to test their weapons. (Courtesy USC Information Sciences Institute) |
The DETER network will simulate the makeup and operation of the entire Internet, from routers and hubs to end users' computer desktops. The testbed will serve as a shared laboratory where researchers from government, industry and academia can put their cybersecurity technologies to the test. The network will be intentionally challenged by malicious codes that range from worms to denial-of-service attacks to programs that attack a network's routing infrastructure.
The testbed, which will eventually consist of approximately 1,000 computers with multiple network interface cards, will be isolated so that the cyberwar can play out freely without impacting the actual Internet. There will be at least three permanent hardware clusters, or nodes, as part of the network. One cluster will be hosted by UC Berkeley, a second by USC-ISI in Los Angeles and a third at ISI-East in Virginia.
Benzel points out that while hackers have been able to use the Internet as their own testbed, the cybersecurity research community has not had a comparable national scale network to fully test their defense programs.
"There is a lot of very good research from the past 10 years that hasn't made its way to commercial products," said Benzel. "I believe strongly that one of the reasons we haven't seen security technology used as much is because there has been a lack of sufficient evidence of the benefits and tradeoffs these new technologies bring."
While the UC Berkeley-led team focuses on designing and building the testbed's infrastructure, a sister project led by UC Davis and Pennsylvania State University will develop testing and evaluation methodologies. That project, called Evaluation Methods for Internet Security Technology, or EMIST, has been awarded $5.34 million by NSF for three years and includes Purdue University and the International Computer Science Institute as partners.
"Science has an essential role in protecting the country's digital and physical infrastructure," said Mari Maeda, acting division director for Advanced Networking Infrastructure and Research at NSF. "Projects such as these demonstrate how NSF contributes both to cutting-edge research and the nation's security."

